Network adapter
The network card, also known as a network board, network
adapter, LAN adapter, physical network interface,1 or its English terms network
interface card or network interface controller (NIC), whose literal translation
from English is "network interface card" (TIR), is a hardware
component that connects a computer to a computer network and that makes it
possible to share resources (such as files,
entire hard drives, printers, and the internet) between two or more computers,
i.e., in a network of computers.
Wikipedia. (September 14, 2021). Network adapter
https://es.wikipedia.org/wiki/Tarjeta_de_red
Attenuation
In telecommunication, the attenuation of a signal, whether acoustic,
electrical or optical, is called the loss of power suffered by it when
transiting through any means of transmission. For example, sound attenuation is the distribution of
wave energy among an increasing volume of air.
Wikipedia.
(September 14, 2021). Attenuation
https://es.wikipedia.org/wiki/Atenuación
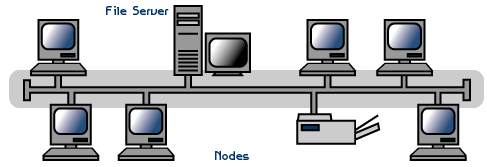
Bus network
A bus network is that topology that is characterized by having a single
communications channel (called bus, trunk or backbone) to which the different
devices are connected. This way all devices share the same channel.
It is the third of the major topologies. The stations are connected by a
single cable segment. Unlike a ring network, the bus is passive, no signal
generation occurs on each node or router. In the bus topology all nodes
(computers) are connected to a common circuit (bus). The information that is
sent from one computer to another travels directly or indirectly, if there is a
controller that routes the data to the correct destination. The information
travels through the cable in both directions at an approximate speed of 10/100
Mbps and has at its two ends a resistance (terminator). A large number of
computers can be connected to the bus, if a computer fails, communication is
maintained, the same does not happen if the bus is the one that fails. The type
of cabling used can be coaxial, twisted pair or fiber optics. In a bus
topology, each computer is connected to a common segment of network cable. The
network segment is placed as a linear bus, that is, a long cable that goes from
one end of the network to the other, and to which each node of the network is
connected. The cable can go through the floor, walls, ceiling or various
places, as long as it is a continuous segment.
Wikipedia. (September 14, 2021). Bus Network
https://es.wikipedia.org/wiki/Red_en_bus
Coaxial cable
The coaxial cable, coaxil, coaxcable or coax, is a cable used to transport
high frequency letric signals that has two concentric conductors, a central
one, called a core, in charge of carrying the information, and an external one
of tubular appearance, called mesh, shielding or braid, which serves as a
reference of earth and return of the currents. Between them is a dielectric
insulating layer, on whose characteristics the quality of the cable will depend
mainly. The whole assembly is usually protected by an insulating cover (also
called an outer jacket).
Coaxial cable was employed in the first transatlantic telegraph cables from
1858, but its theory was not described until 1880 by the English electrical
engineer and mathematician Oliver Heaviside, who patented its design that same
year.
Information retrieved and created by Wikipedia
(https://es.wikipedia.org/wiki/Cable_coaxial)
Optical fiber
Fiber optics are the technology used to transmit information in the form of
pulses of light using fiberglass or plastic wires, over long distances.
Optical fibers measure around the diameter of a human hair, and when
combined into a fiber optic cable they allow more data to be transmitted over
longer distances and faster than other media. It is the technology that allows
to provide homes and companies with Internet, telephone and fiber optic TV
services.
Information retrieved and created by Verizon
(https://espanol.verizon.com/info/definitions/fiber-optics/)
UTP
Inside a UTP cable is up to four twisted pairs of copper
wires, enclosed in a protective plastic cover, with the greater number of pairs
corresponding to more bandwidth. The two individual wires in a single pair are
twisted around each other, and then the pairs are twisted around each other, as
well. This is done to reduce crosstalk and electromagnetic interference, each
of which can degrade network performance. Each signal on a twisted pair
requires both wires.
SearchNetworking. (September 2019). Unshielded Twisted
Pair (UTP)
https://www.techtarget.com/searchnetworking/definition/Unshielded-Twisted-Pair
Network hub
A hub is a small, rectangular, inexp-or-good device that
joins multiple network-enabled devices. They are often made of plastic and
receive power from a common power outlet.
The purpose of a hub is to form a single network segment
in which all devices can communicate directly with each other.
Until the early 2000s, Ethernet hubs were widely used for
home networks due to their simplicity and low cost. While broadband routers have
replaced them in homes, hubs still have a useful purpose.
Kevin Stein. (2 years ago). What are network and ethernet hubs?
https://androidzeal.com/red-internet/que-son-los-concentradores-de-red-y-ethernet/
Datagram
A datagram is a data packet that constitutes the minimum
block of information in a datagram switching network, which is one of two types
of packet switched communication protocol used to route these information units
between nodes in a network over different routes, so it is said to be
non-connection-oriented. The alternative to this packet switching is the
virtual, connection-oriented circuit.
Wikipedia. (
January 28, 2021). Datagram.
https://es.wikipedia.org/wiki/Datagrama
MAC address
When you're checking your network for who's connected to
it, the programs you're going to use will show you certain information about
the connected devices. For example, you'll know its manufacturer, its IP
address, and its MAC. Usually it does not cost too much to identify each device,
but sometimes we have so many that things get a little complicated.
Yúbal Fernández, engadget. (October 6, 2017) . What is the MAC address of your computer,
mobile or any device?
https://www.xataka.com/basics/que-es-la-direccion-mac-de-tu-ordenador-del-movil-o-de-cualquier-dispositivo
Protocol
In computer science and telecommunication, a
communications protocol is a system of rules that allow two or more entities
(computers, cell phones, etc.) of a communication system to communicate with
each other to transmit information by means of any type of variation of a
physical magnitude. These are the rules or standard that defines the syntax,
semantics and synchronization of communication, as well as possible methods of
error recovery. Protocols can be implemented by hardware, by software, or by a
combination of both.
Wikipedia. (April 5, 2021). Communications protocol.
https://es.wikipedia.org/wiki/Protocolo_de_comunicaciones
DNS
The Domain Name System (DNS) is the internet's telephone
directory. People access information online using domain names, such as
nytimes.com or espn.com. Web browsers interact using Internet Protocol (IP)
addresses. DNS translates domain names to IP addresses so that browsers can
load Internet resources.
Cloudflare. (2021) What is DNS?
https://www.cloudflare.com/es-es/learning/dns/what-is-dns/
Server
A server is a system that provides resources, data,
services, or programs to other computers, known as clients, over a network. In
theory, servers are those computers that share resources with client machines.
There are many types of servers, such as web servers, mail servers, and virtual
servers.
Information retrieved and created by PAESSLER.
(https://www.paessler.com/es/it-explained/server)